Best ways to send an encrypted email in 2021
Best ways to send an encrypted email in 2021
A detailed guide on how to purchase, install and configure your email client to enable end-to-end encryption and provide an additional layer of trust for you and your recipients.

TL;DR
Buy and install the S/MIME certificate on your email client.
Table of Content
- What is end-to-end encryption and what’s RSA?
- Types of email encryption and why privacy matters
- Differences between PGP, GPG, and S/MIME
- What is Certificate Authority and why it matters
- Who sells S/MIME certificates and what’s the difference?
- Pricing
- How to issue a certificate request on Mac
- How to purchase your certificate with GlobalSign
- Levels of S/MIME certificates and trust
- What’s the difference between Signing and Encrypting your email
- What email clients support S/MIME
- How to install S/MIME on iOS Mail client
- How to install S/MIME on macOS Mail client
- How to force signing and encryption with S/MIME by default on iOS
- Hardware options
- Enterprise S/MIME encryption
- What happens when you need to renew your certificate?
- What to do when your certificate and the private key were compromised or lost?
What is end-to-end encryption and what’s RSA?
You have heard of end-to-end encryption in many different services ranging from Zoom to Signal. To truly understand why it matters you need to know how the Internet works and how your data is being sent from one device to another, from sender to recipient. The usual route would originate at your computer or a smartphone and continue to your ISP, which in their turn would use another commercial ISP and so on until it reaches the exchange point (IXP), where multiple commercial ISPs, data centers, and service providers exchange data of their services and users.
And you guessed it right, most of the time when your data is being sent from your device to another device or another server, it is most likely unencrypted and can be read via plain text format or decoded using protocol specifications. That’s why so many websites and service providers are switching from HTTP to HTTPS. The difference is in one letter, “S”, and it stands for Secure.
Conceptually, it is a way for software to encapsulate their data in a given protocol in a way where only the sender and recipient would be able to read the said data. And it is possible because of Cryptography, in particular, something that was created in 1977 and is called RSA.
So end-to-end encryption is a version of encryption where only sender and recipient can decrypt the data that’s being sent, and no parties in between have access to decrypted data. This effectively gives you your privacy and protects your data from the MitM vector of attack.
Types of email encryption and why privacy matters
Just like HTTPS relies on TLS to provide a layer of security, email systems that use a variety of protocols like SMTP, IMAP, POP3. None of them really have any extensive ways to encrypt and secure your messages along the way from your device to the servers and then to the rightful recipient.
Same way HTTP uses TLS/SSL, email protocols have alternatives to provide users with more security compared to original protocols. Most of these extensions work on the Presentational layer of the OSI model.
Here they are (in random order):
Emails encryption is the second biggest privacy moat after the Web. Companies like Google have been mining your data for decades by offering free Gmail services where you as a user became a product.
Differences between PGP, GPG, and S/MIME
PGP was created in 1991 and later, a version of it was implemented in the OpenPGP that became free of patent issues of the original PGP. It is open-sourced and licensed.
GPG was created in 1999 and is designed as a fully interchangeable replacement for the PGP protocol. It technically implements a bigger variety of tools and instruments and does not depend on PGP legally.
S/MIME uses a similar concept as both PGP and GPG, things like public-key certificates and asymmetric encryption, but the main difference is in the additional layer of trust. Much like for SSL, where you would need to issue a certificate from a trusted authority, the same principle is applied to S/MIME, where you would issue a certificate for your email address in the same fashion as issuing an SSL certificate for your domain name. MIME format is defined as application/pkcs7-mime.
What is Certificate Authority and why does it matter
Certificate Authority is a key differentiator between the self-signed certificates and the certificates you can trust. Certificate Authorities are at the crossroads of technical and legal aspects of issuing a certificate.
Most of the consumer computers and phones come with a set of pre-installed root certificates of Certificate Authorities. These root certificates enable your browser, email clients, and other software to validate and confirm the origin of the data and establish trust.
Whenever you purchase a certificate for your website or your email, you ask Certificate Authority to issue a Certificate to your name, and this newly issued certificate will be validated using root certificates on other computers.
Who sells S/MIME certificates and what’s the difference?
There are a lot of vendors who can sell them, but there are only a few that can be trusted and valid since only these vendors would guarantee client email software, and would be able to recognize such certificates and establish trust:
- EnTrust
- IdenTrust
- Sectigo (formerly Comodo)
- GlobalSign
- DigiCert (formerly Symantec)
- SSL.com
- Actalis (free for personal use)
Before choosing one of the Certificate Authorities, make sure to check them for security incidents and/or any other known issues.
Pricing

How to issue a certificate request on Mac
Before you proceed with your S/MIME certificate purchase, you will first need to issue a certificate request unless you want to go with the hardware options.
Issuing a certificate request ensures that you create a private key first and then let your Certificate Authority know that you have issued one via Certificate Signing Request (CSR).
- Open Keychain Access from your Application/Utilities on your Mac
2. Open Certificate Assistant from the top menu in the left corner**.**
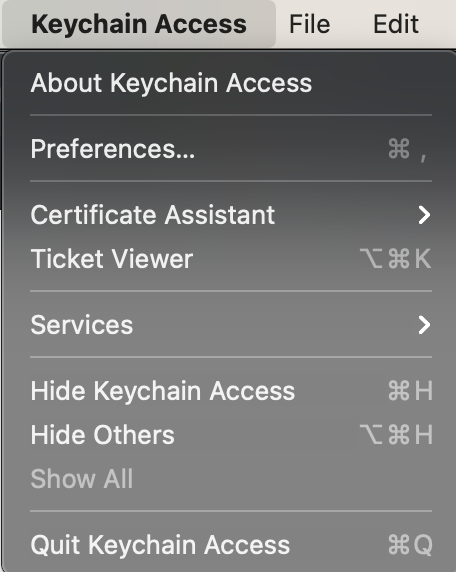
3. Select Keychain Access –> Certificate Assistant –> Request a Certificate From a Certificate Authority from the menu.
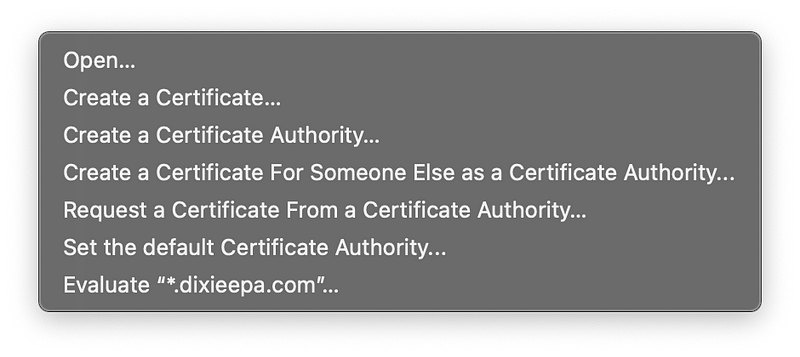
4. Enter the email address
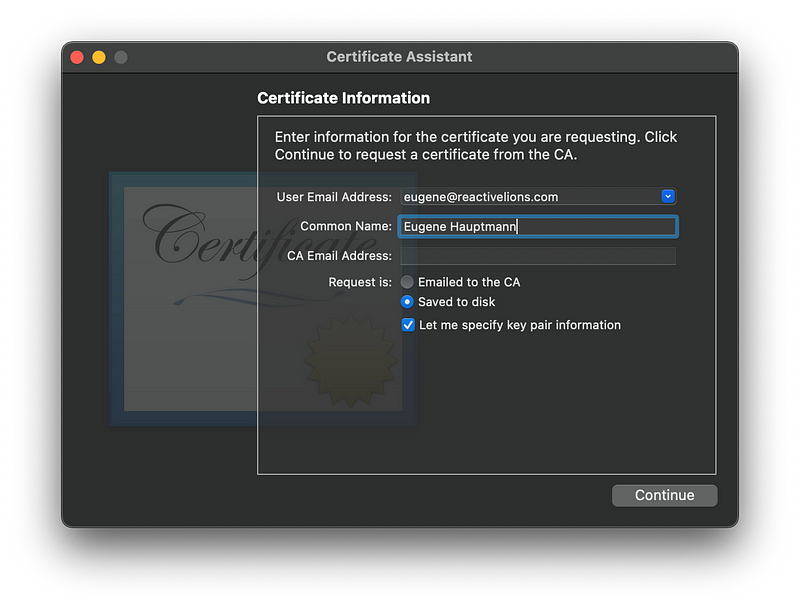
5. Check saved to disk and let me specify key pair information
6. Pick the filename and save
7. Set key size as 2048 bits and set algorithm to RSA
8. Click continue
9. And done
Inside the file, you’ll find the request itself.
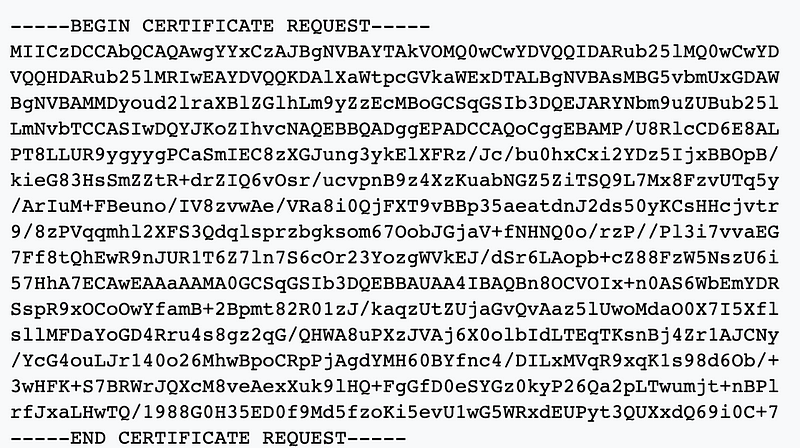
If you prefer a command-line interface and you have OpenSSL installed, you can do the same thing:
openssl req -new -newkey rsa:2048 -nodes -out servername.csr -keyout servername.key
How to purchase your certificate with GlobalSign
- Go to https://shop.globalsign.com/en/secure-email
- Pick the type of your certificate
- Fill out the form with your contact details, your organization details, and create your login information. Make sure to check “I will use a PKCS10 to generate the public/private keypair during certificate pickup.” This means you will be able to submit your CSR request.
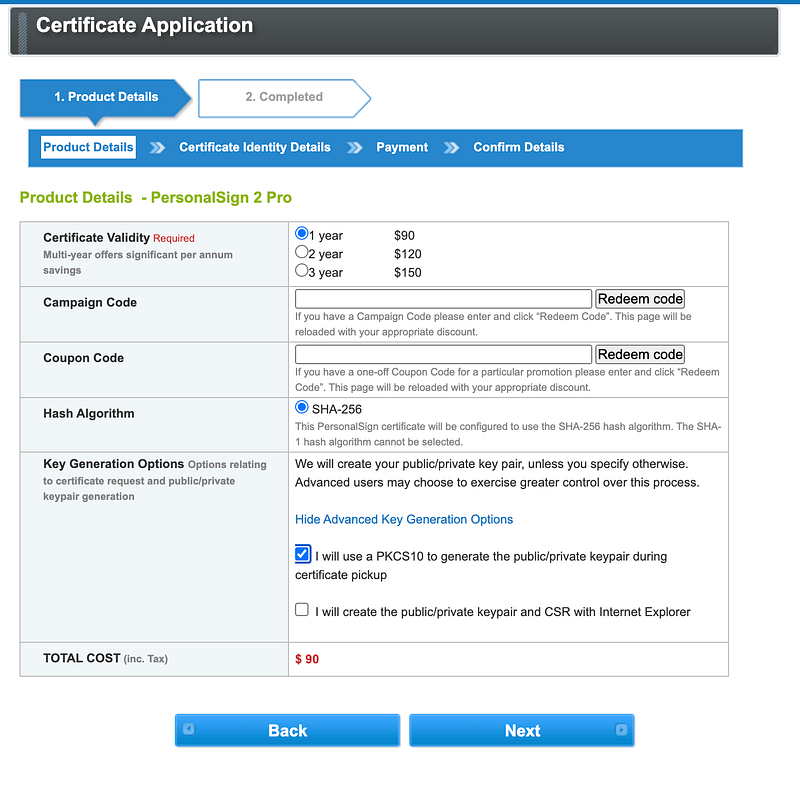
4. Confirm your account via email
5. Create your Certificate Identity Details
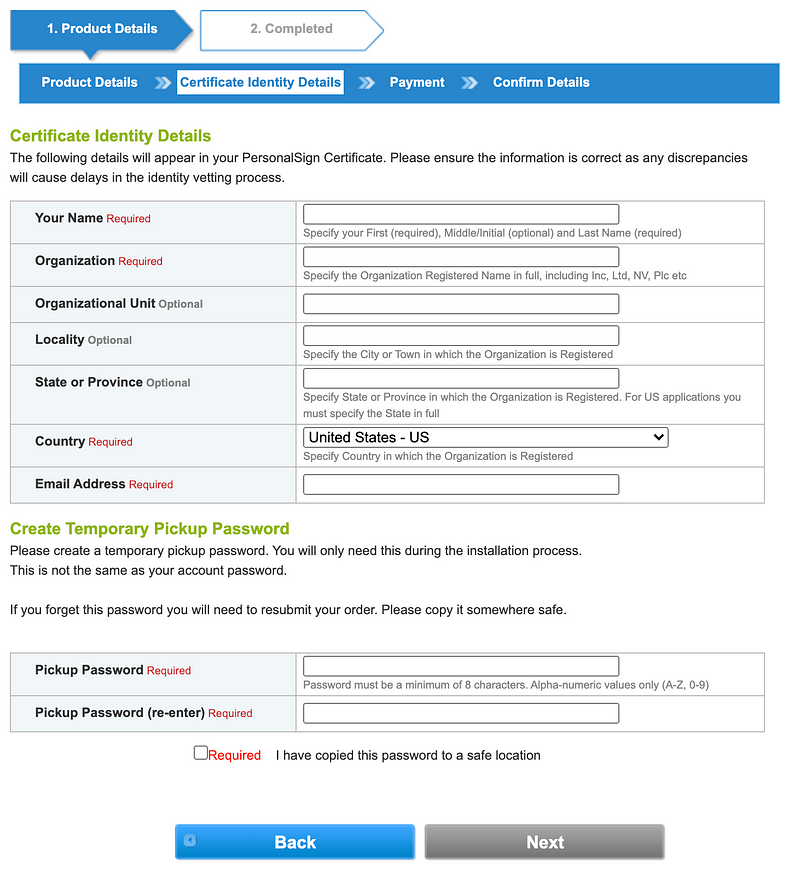
6. Add your payment method
7. Confirm order details
8. Approve application via email

9. Pass the validation via phone or mail. Here are some other options:
1. We can send a letter to the registered address of the Applicant. This will contain a password for you to confirm via phone or by emailing us; or
2. The organization's telephone number can also be confirmed via a letter from a registered accountant or lawyer. This would need to be on their letter headed paper, and simply confirm a telephone number for your organization on which we can reach you; or
3. We can accept a recent telephone bill in the name of your organization (or the name of a listed director), showing a telephone number on which we can reach you; or
4. If you have a publicly trusted certificate (GlobalSign AATL, PersonalSign 2 Pro or equivalent) you can digitally sign a document or an email with your certificate confirming the details in the order (order number) and authorizing us to issue the certificate. If using this method your certificate used for signing must be in your name and include the name of the organisation (Common Name = your name; Organisation = your organisation name). The signed document or email will then be escalated to our Compliance team for further internal review prior to acceptance.


10. Once you send your verification code, you’d be able to pick up your certificate, after submitting CSR.
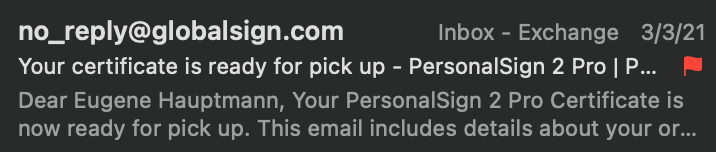
11. Pick up your certificate using the pickup password you’ve created before.
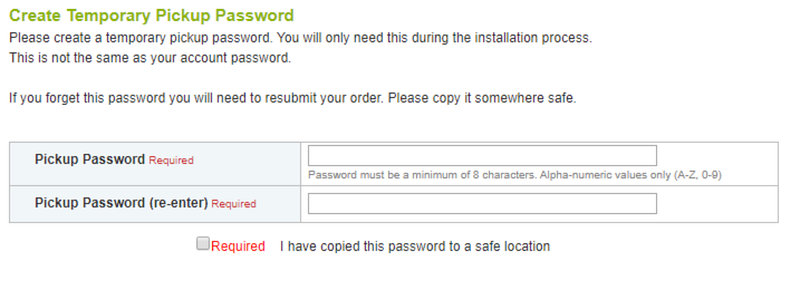
12. Enter CSR and download your brand new certificate!
Levels of S/MIME certificates and trust
The main difference in types of email certificates is in the purpose of their use: personal or business.
On the technical level you can grade them in the following order:
- Email address only
- Email address, first name, last name
- Email address, first name, last name, company name, company address
Encryption strength:
- 1024 bits (outdated)
- 2048 bits
- 4096 bits
- and more
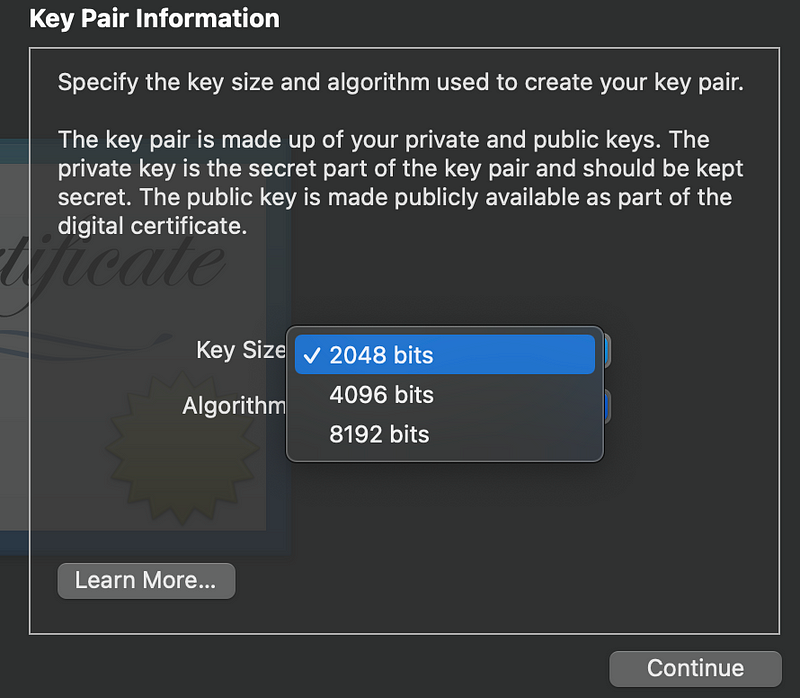
Length:
- 1 year (recommended)
- 2 years
- 3 years
Bunding:
Some Certificate Authorities would bundle additional uses like document signing or code signing into the main certificate.
What’s the difference between Signing and Encrypting your email
Signing is the simplest use case for your S/MIME certificate. It doesn’t prevent MitM vector, but serves a single purpose, to verify that a particular email originated from you and was not sent by a malicious actor like a spammer, or that your email server was compromised.

Encryption is the second use case when after exchanging signed emails between the two parties, you can use the recipient’s certificate to encrypt the content of your email body, and this makes reading your email very complicated for any third party who might intercept your email.

Which email clients support S/MIME
The majority of email clients support S/MIME certificates out-of-the-box.
Desktop:
- Mozilla Thunderbird
- Microsoft Outlook
- The Bat
- Apple Mail
- Microsoft Mail
- etc
Mobile:
- Gmail (only hosted S/MIME)
- Microsoft Outlook (only for paid Office365 customers)
- Apple Mail
- Mailbox
How to install S/MIME on an iOS Mail client
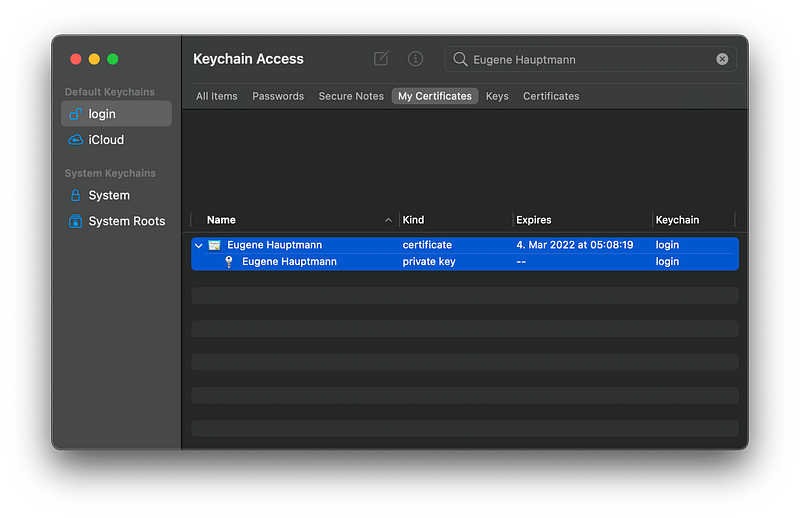
- Find your certificate and private key in Keychain Access on your Mac.
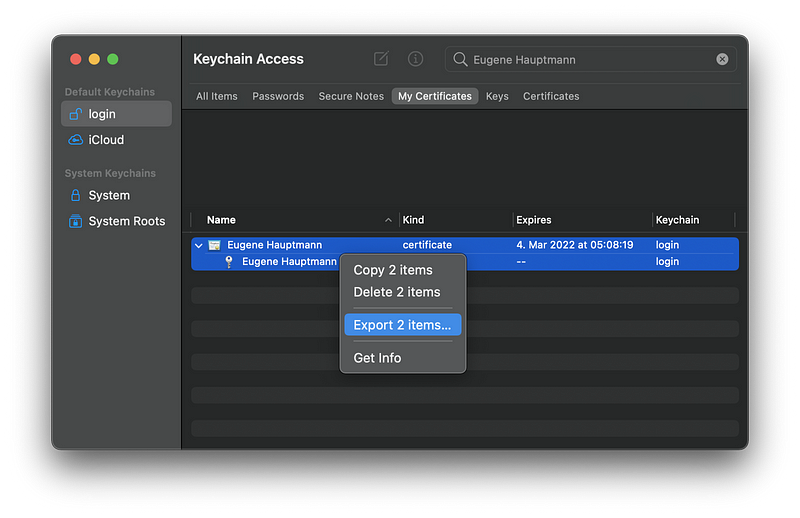
2. Select both certificate and private key, right-click, and select Export 2 items.
3. Save certificate.p12 and remember the password you used to create it. You will need it on your iOS device next.
4. Email this certificate to yourself or AirDrop it to your iOS device.
5. When you open certificate.p12 on your iOS device it will appear in your Settings.
6. Go to Settings and select your newly downloaded certificate and click Install.
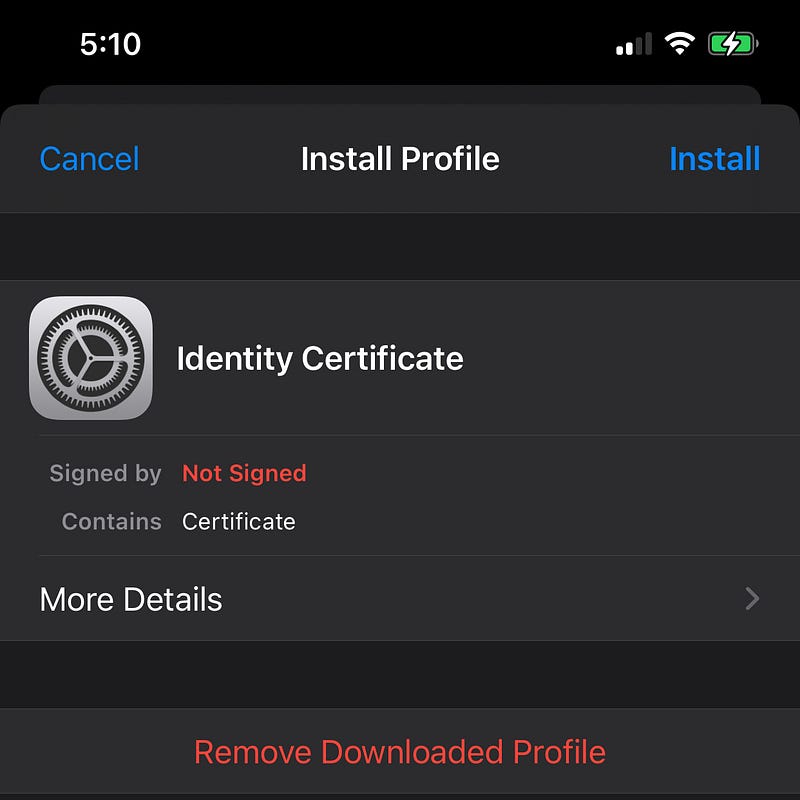
7. Confirm installation again and click Install Now.
8. Enter your device’s PIN code and click Next.
9. Click Done once the certificate is installed.
Next, you want to make sure your device signs your emails with an appropriate certificate, here are the steps on how to do it:
- Go to Settings
- Select Accounts & Passwords
- Click on the email account you want to setup
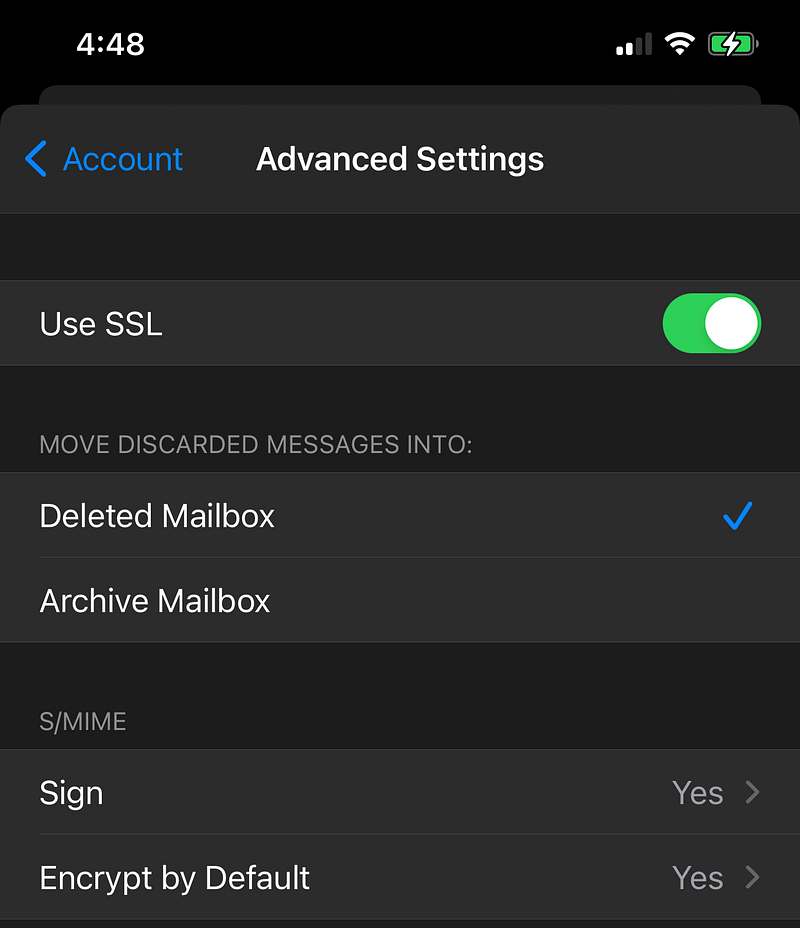
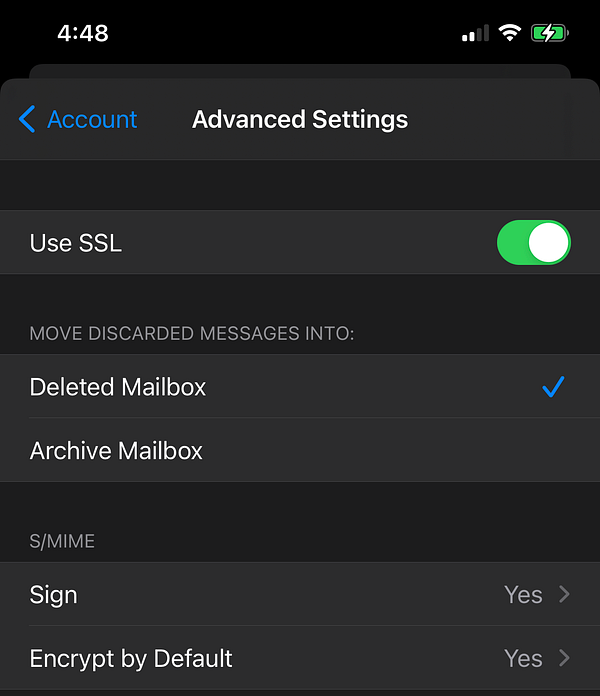
- Go to Account –> Advanced
- Scroll down to the S/MIME section
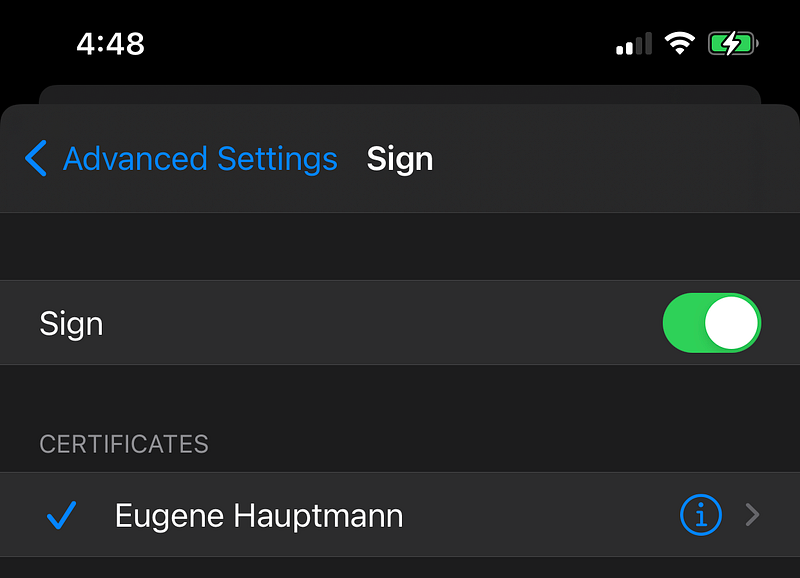
- And configure both Signs and Encrypt by default options with your certificate.
How to install S/MIME on macOS Mail client
If you’re using email on the same computer where you issued your CSR and downloaded your certificate, then you’re all set!
If not, please follow the previous section to download both the certificate and private key to your Mac.
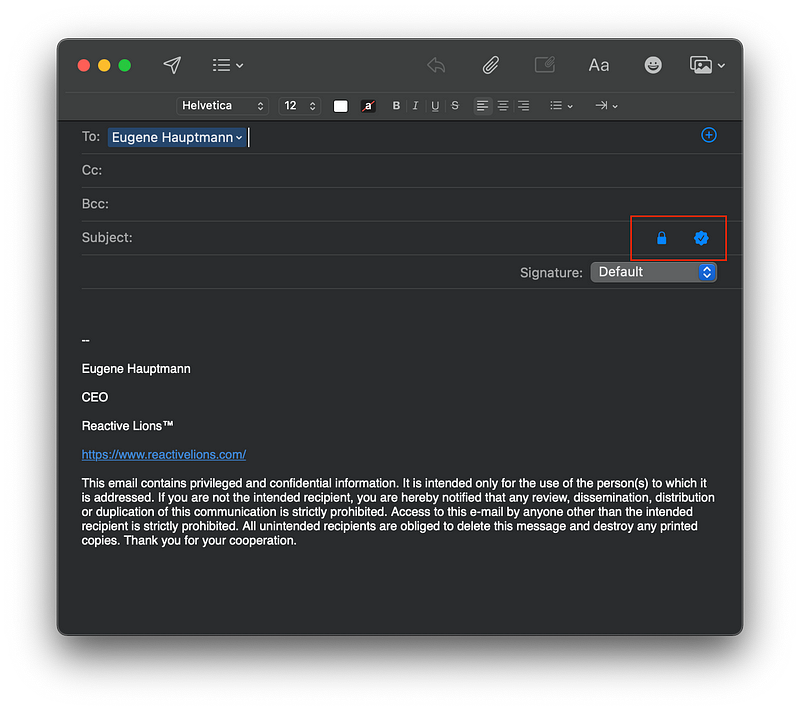
To compose a new email and encrypt it, please click on the lock icon, make sure that you have your recipient's certificate downloaded. See the red rectangle below.
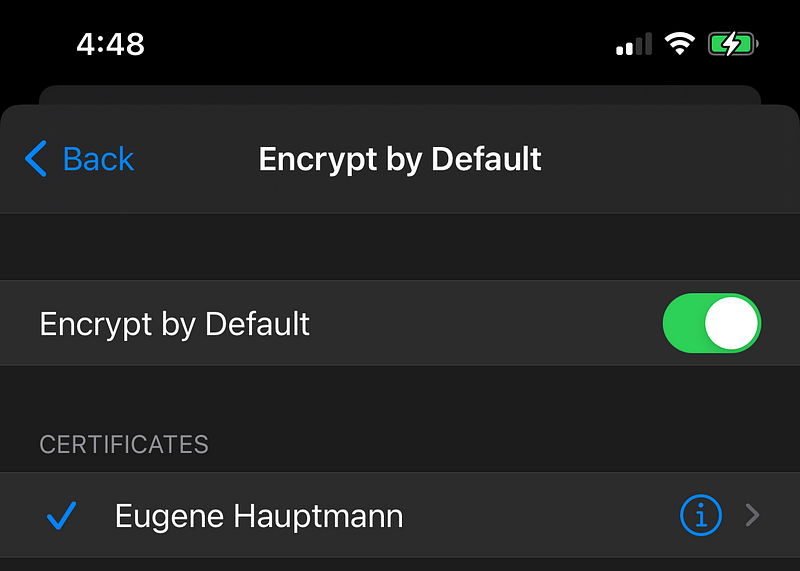
How to force signing and encryption with S/MIME by default on iOS
- Go to Settings
- Then to Accounts & Passwords
- Click on the email account you want to setup
- Go to Account –> Advanced
- Scroll down to the S/MIME section
- And go to Encrypt by Default option
- Enable encryption
- And pick your new certificate
Hardware options
You can use hardware solutions like YubiKey to install your private key and certificate. The hardware option would give you more protection against compromising access to your private key, by putting it to the hardware token and adding an extra layer of physical protection.

Enterprise S/MIME encryption
Most Certificate Authorities would want to verify your company either by calling you or mailing you a paper code via post.
- A phone call would happen sometime within a week, depending on your vendor
- A physical mail would arrive at your office within two weeks, depending on your location in the US
Important steps your CIO should undertake are to monitor the validity of the company’s certificates regularly and to report any of the certificates that were compromised, so they can be revoked as soon as possible. Make sure to use automated solutions to validate corporate certificates continuously.
Another important thing to mention is making sure the email clients you use have to be up to date and not compromised. Check this incident from 2018 for an example.
If you implement a BYOD policy we strongly recommend implementing an MDM solution to manage your devices from one place.
What happens when you need to renew your certificate?
If you still want to read your old encrypted emails, make sure NOT to delete your old expired certificates from your devices. If you do delete them, you won’t be able to decrypt and read old emails.
Proceed as usual and purchase another certificate and install it on your devices along with the old certificates.
What to do when your certificate and the private key were compromised or lost?
Check the documentation of your Certificate Authority and reach out to them to revoke your certificate.
For example, GlobalSign lets you revoke it yourself from the same interface.
About the author

Eugene is a faith-centric technologist, a serial entrepreneur, angel investor, advisor, and mentor.
He is the founder and CEO of REACTIVE LIONS INC. where he is implementing his vision of faith-driven entrepreneurship in the tech world. He is currently running a team of over 40 talented engineers across the US.
Eugene is the expert in building tech teams and he is a chief architect of scalable software products. His experience goes beyond B2B and B2C in multiple industries like Cyber Security, Deep Tech, FinTech, Media, AI, ML, Data platforms, Marketplaces, Wellness, Healthcare, Space, M&A, and more.
Contact us to learn how we can help your business.
Disclaimer
We are not affiliated, associated, authorized, endorsed by, or in any way officially connected with the GlobalSign or any other Certificate Authority.
All product and company names are trademarks™ or registered® trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
Limitation of warranties
The information in this article is provided “as is” without any representations or warranties, express or implied. REACTIVE LIONS INC. makes no representations or warranties concerning the information in this article.